
Hello there! I'm Yin Moe Aye.
I am a year old IT student, an aspiring cybersecurity expert as well as a tech enthusiast.
About
- 2008
- 2019
- 2022
Skills
Web development
- HTML
- CSS
- Javascript
- PHP
- Bootstrap
- jQuery
- React
Mobile development
- Java
- Android studio
- Adobe XD
- Firebase
Additional skills
- Python
- Java
- C++
- HackerRank
- Kattis
- HTB Academy
Coding Projects
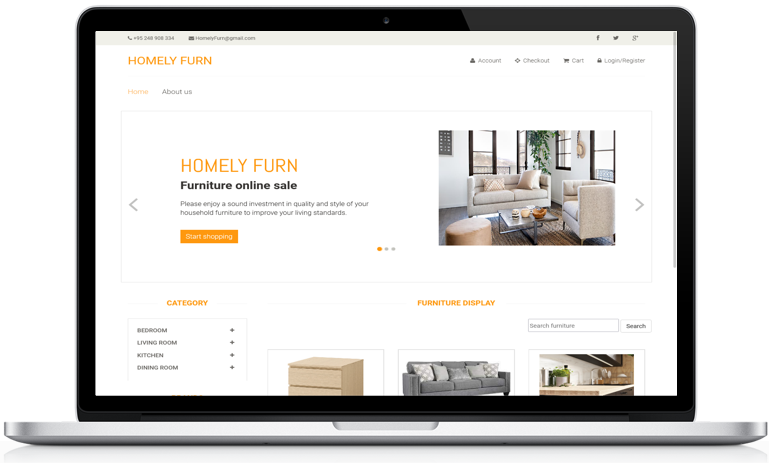
Homely Furn
An online furniture shopping system built with frontend framework Bootstrap and backend language PHP
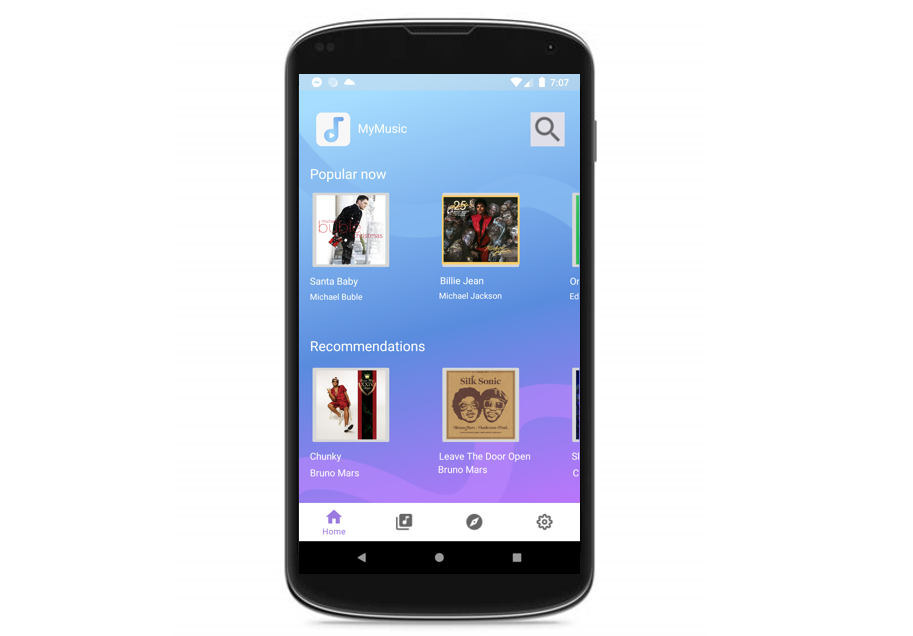
MyMusic
A mobile music player app created with Java using Android Studio
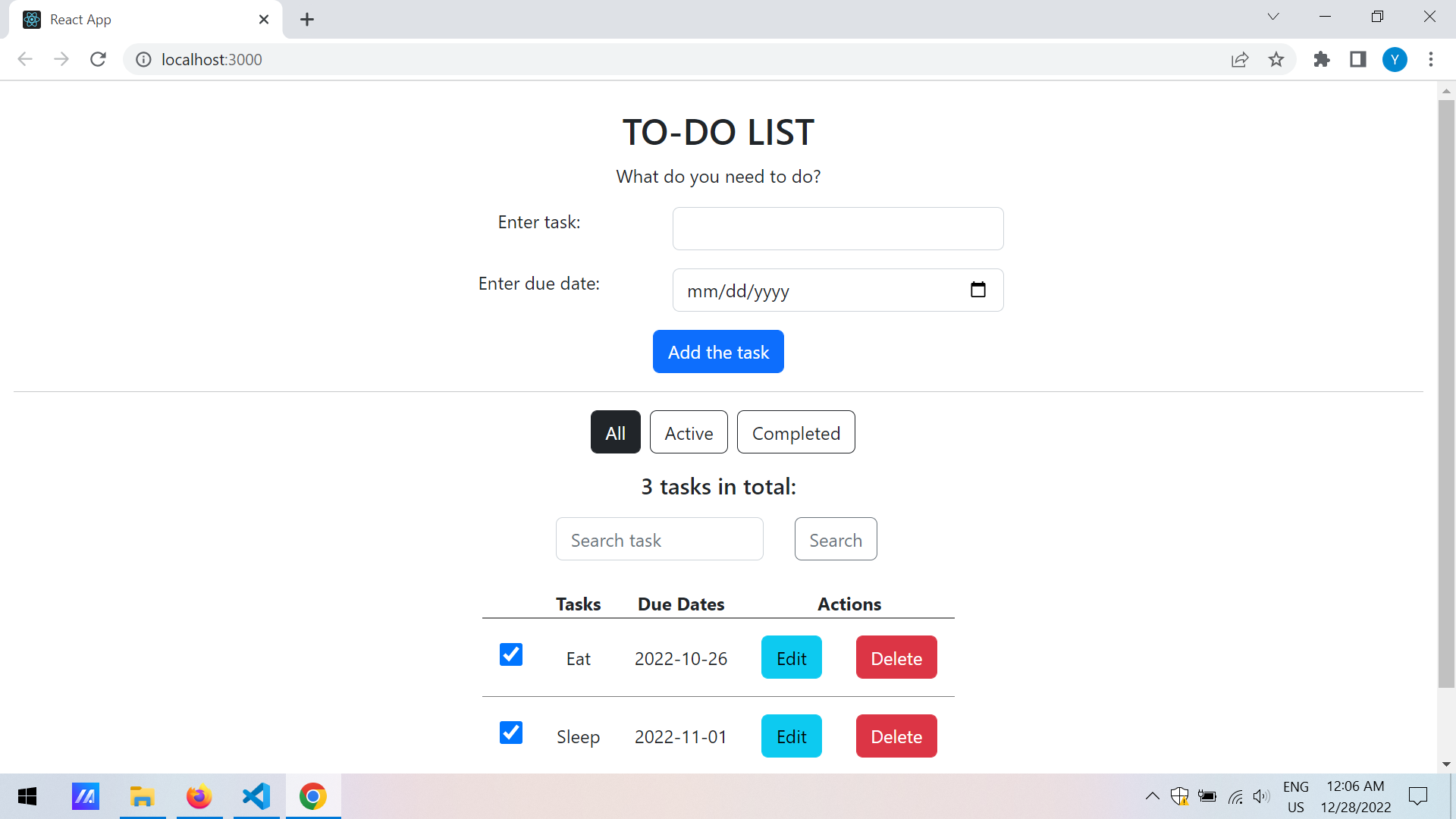
To-Do web app
A to-do web app developed with React and Bootstrap front-end frameworks
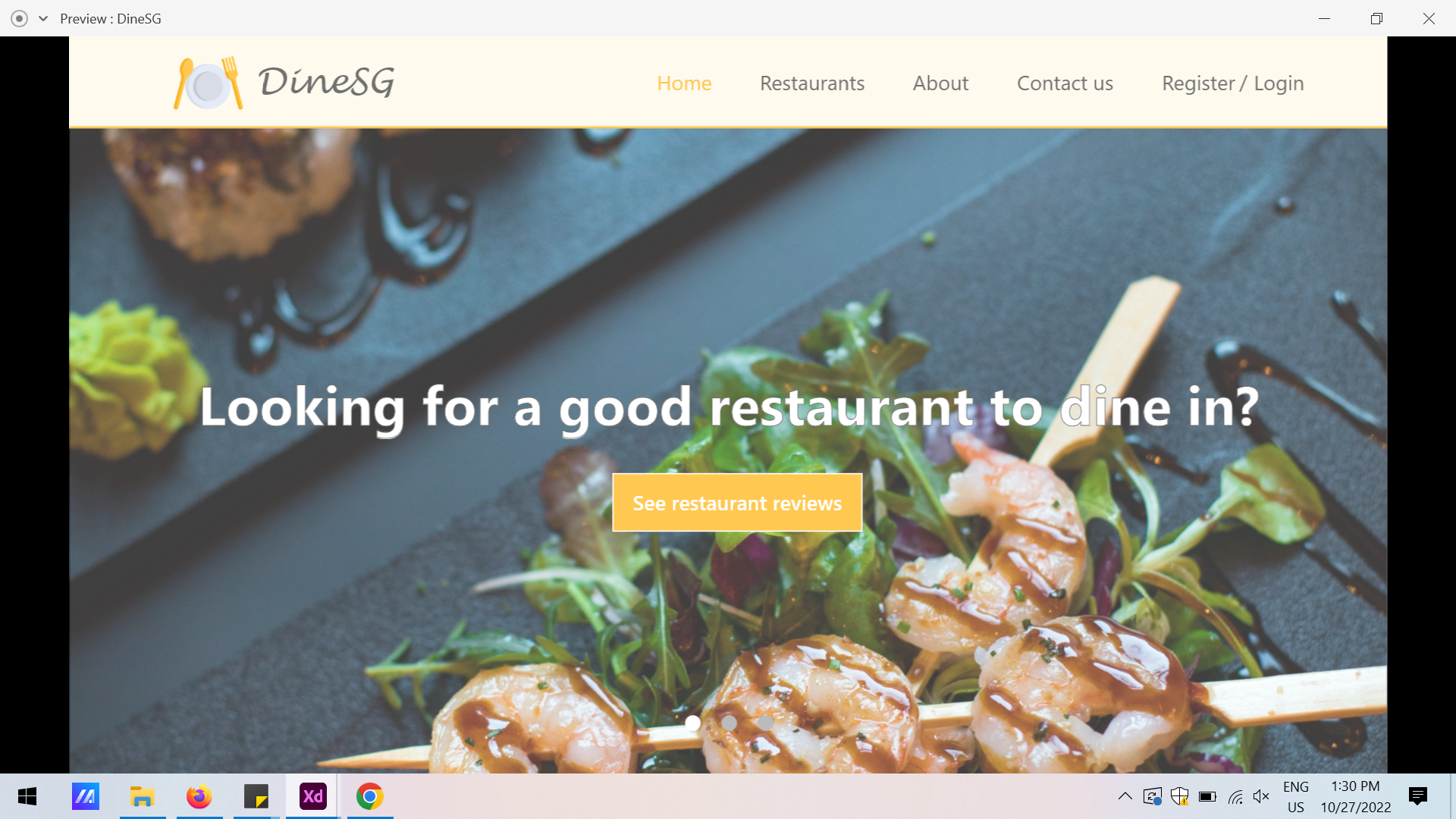
DineSG
A web app developed with Astro, CSS, Javascript and MySQL
Other Technical Projects in TP
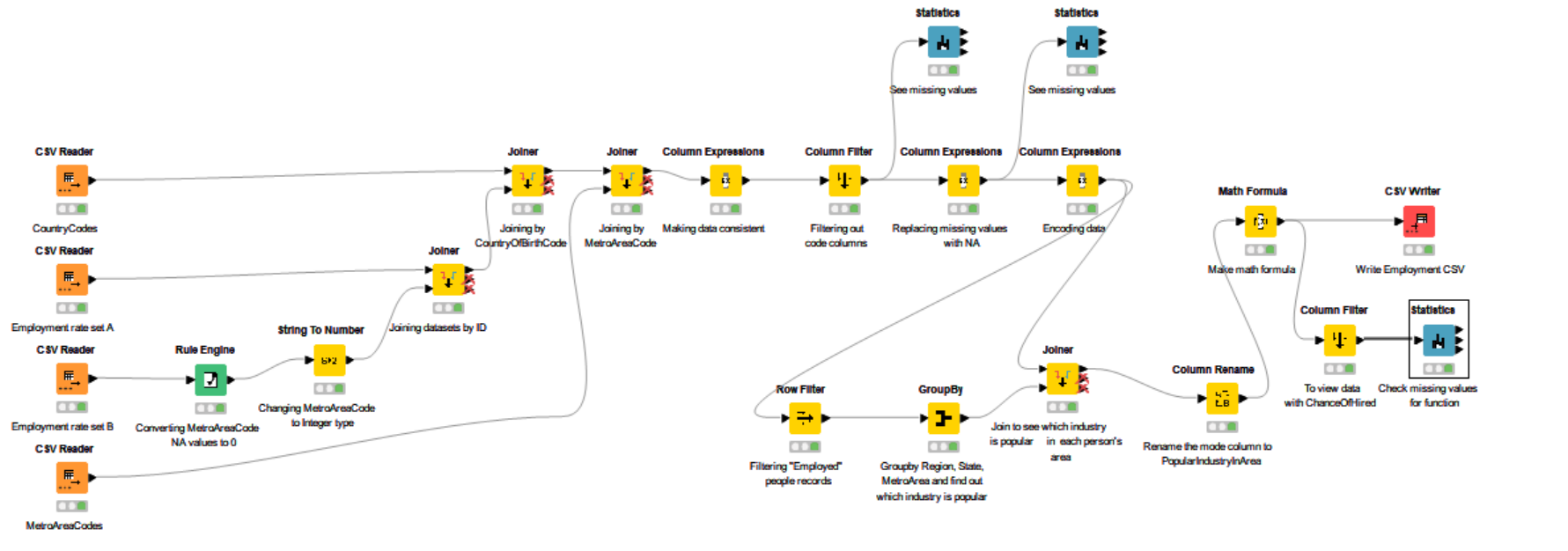
- Knime is a data analytics platform where users can create, execute and inspect visual data flows without any coding.
- The picture on the left shows data cleaning process(making data consistent, handling missing values, encoding data) and Mathematical formula making on employment dataset in USA after Great Recession of 2009.
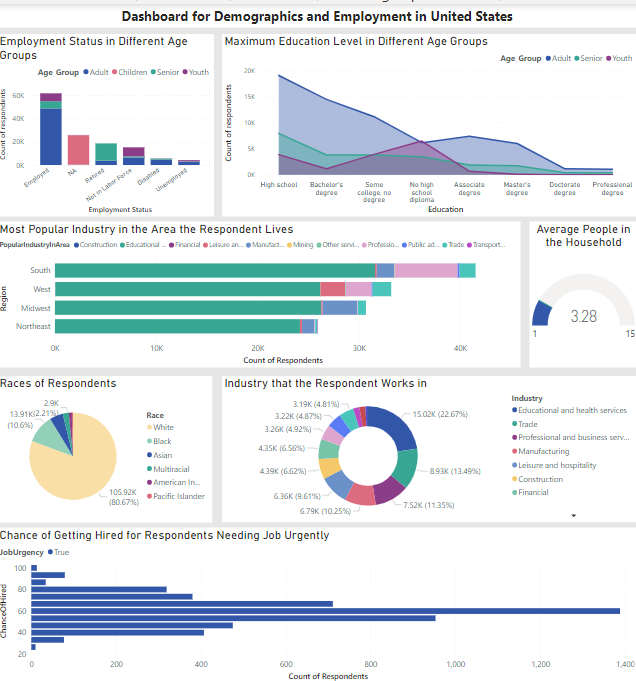
- Power BI is an interactive data visualization software with focus on business intelligence.
- The dashboard on the left is the result of data visualization after data cleaning in Knime.
- Based on the data visualization, decisions and suggestions were derived on how to improve employment rates after recession.
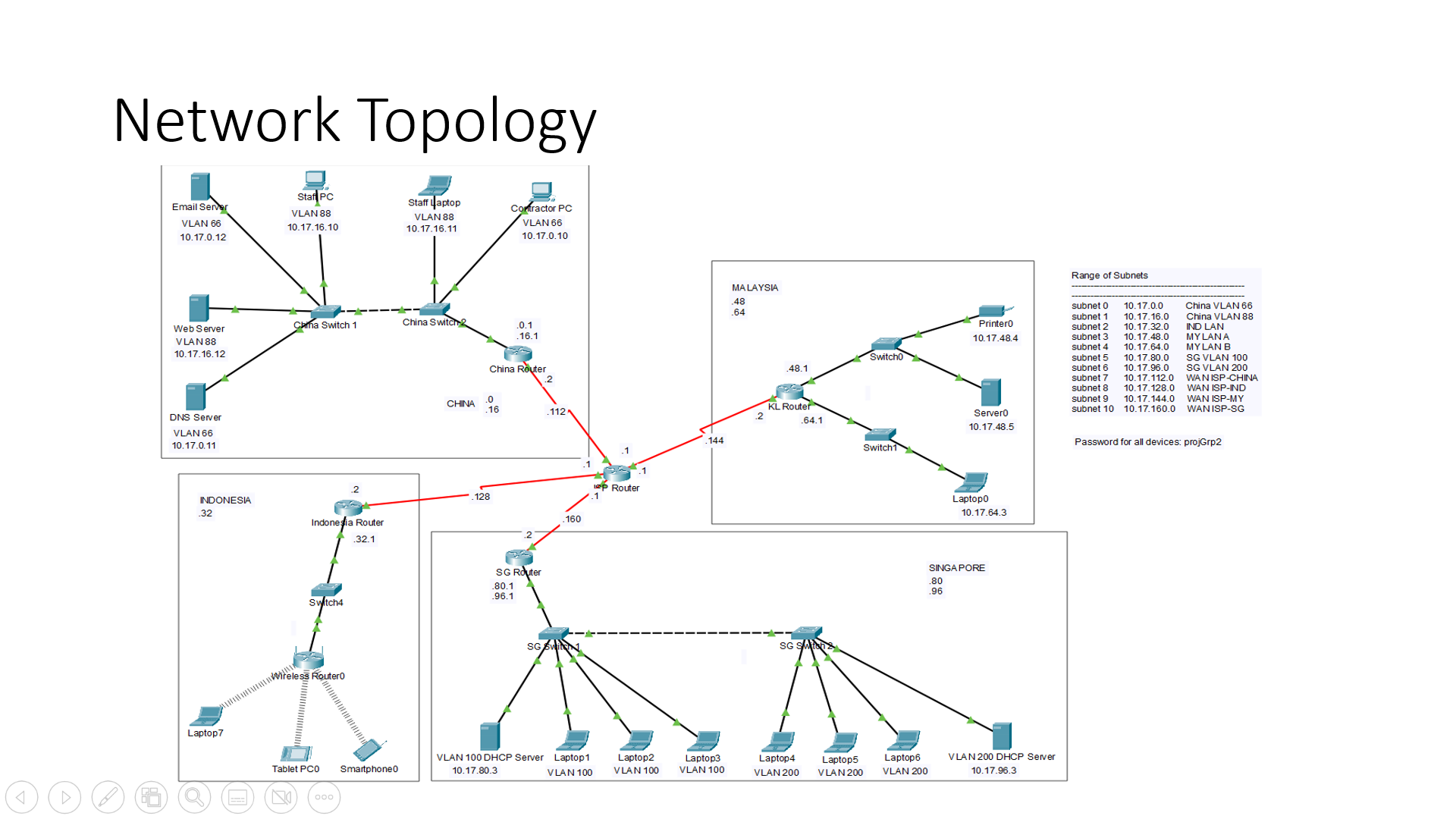
- Cisco Packet Tracer is a network simulation tool that allows users to practise network topologies and IoT in virtual labs.
- The Network Technology project entails calculation of IP adddress subnetting, connecting a business network over LANs and WANs and setting up each network devices in Command Line Interface(CLI).
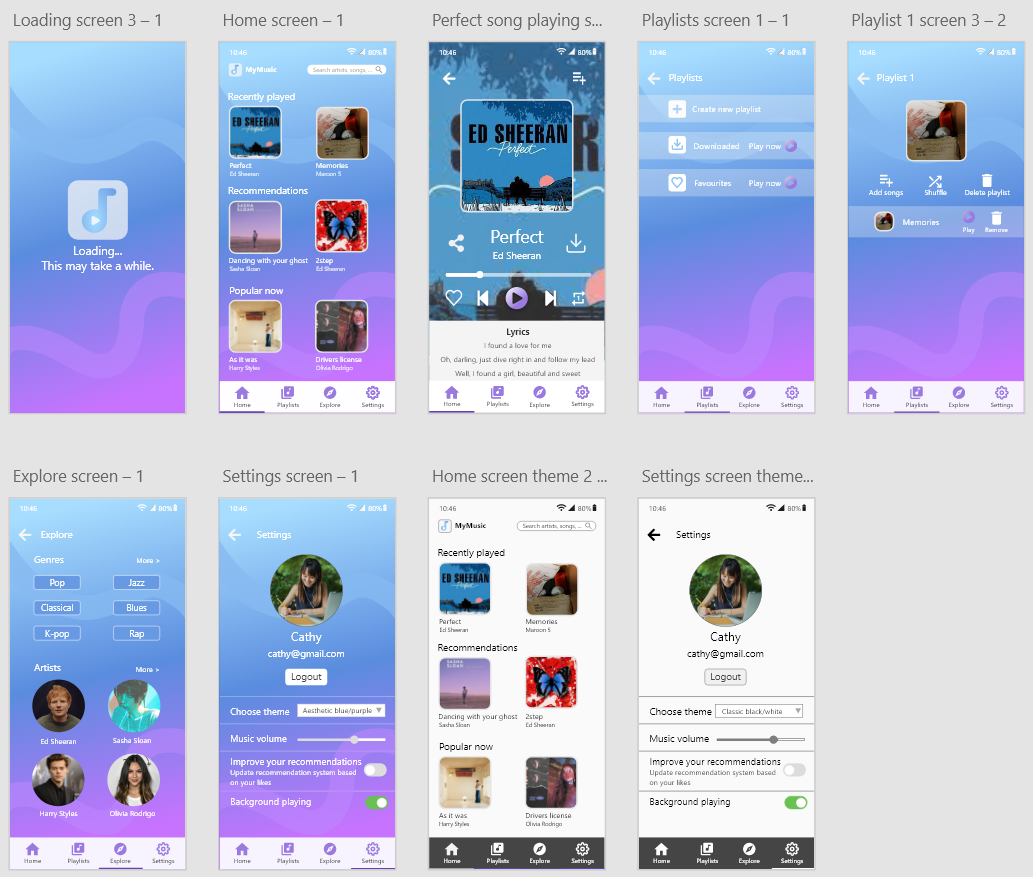
- Adobe XD is a vector design tool for creating web and mobile app prototypes.
- These screens are part of the music player prototype.
- App features include playing music, adding to playlist, favourites, shuffling, looping, downloading songs, sharing songs via social media, searching songs by artists, song names or genres, and changing app themes.
- The final product MyMusic developed according to the hi-fi prototype can be tested in the Coding Projects section.
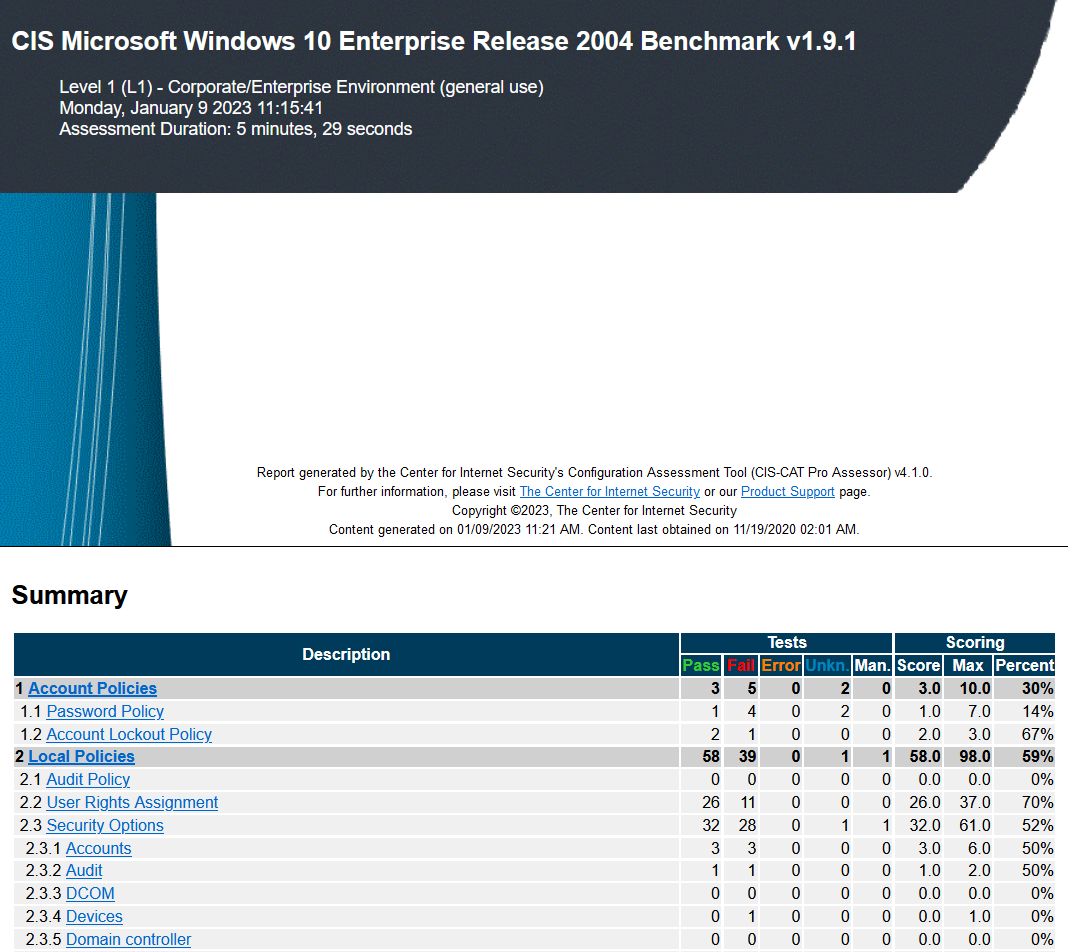
- The CIS Benchmarks are prescriptive configuration recommendations for more than 25+ vendor product families.
- The IT System Security Essentials project requires us to create a Windows 10 virtual machine in Oracle VM VirtualBox according to project specifications.
- The VM was later assessed using CIS Benchmarks Tool and changed configurations to harden the system.
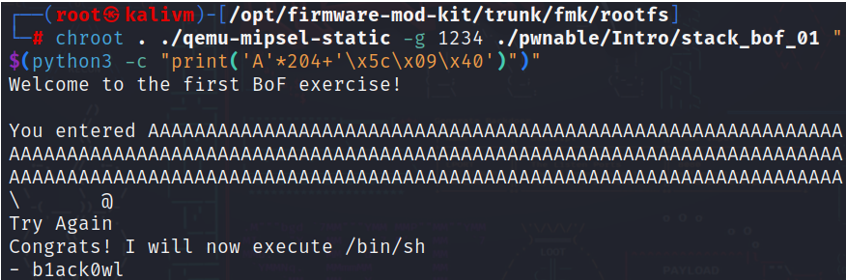
- Kali Linux is a Debian-based Linux Operating System distribution designed for digital forensics and penetration testing.
- In Ethical Hacking and Intrusion Prevention module, we learnt network reconnaisance using Nmap, vulnerability exploitation using Metasploit, privilege escalation and lateral movement.
- The EHIP project for my group was holding a workshop educating our fellow classmates on "Firmware Hacking". In the workshop, GNU Debugger was used to do reverse engineering and demonstrate the exploitation of buffer overflow vulnerability in Damn Vulnerable Router Firmware (DVRF).
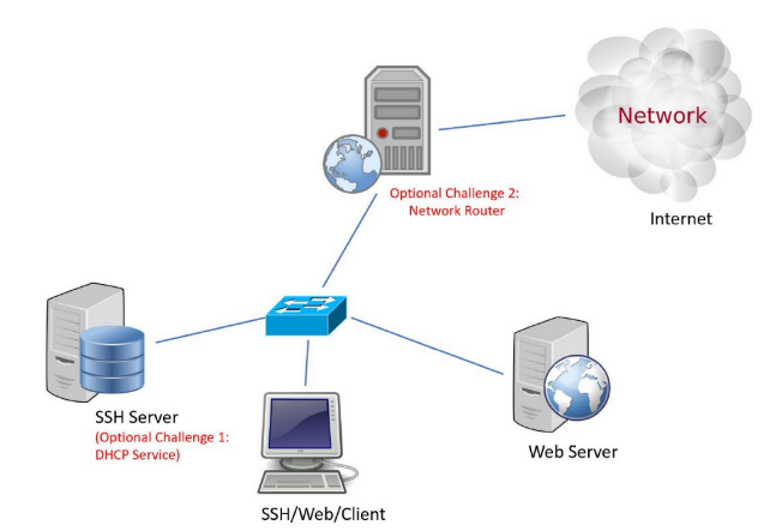
- Red Hat and CentOS are also Linux distributions used for enterprise servers and workstations because of their long-term stability.
- The Servers Administration & Security project was to configure SSH, Web servers, a client workstation and a network router in CentOS VMs using Oracle VM VirtualBox.
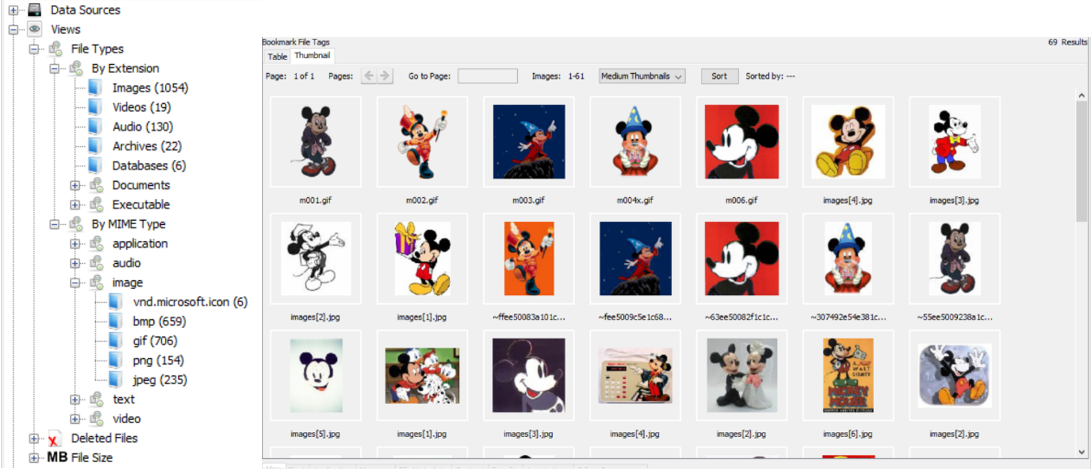
- Autopsy is a digital forensics platform and graphical interface to The Sleuth Kit and other digital forensics tools.
- Autopsy was used to investigate a project case study in which Fred was accused of unauthorized use of copyright Mickey Mouse images.
- The project scope entails acquisition and making exact copy of Fred's disk image, authentication to make sure the image is not changed during the forensic process, analysis using 5 WH questions and reporting the findings.
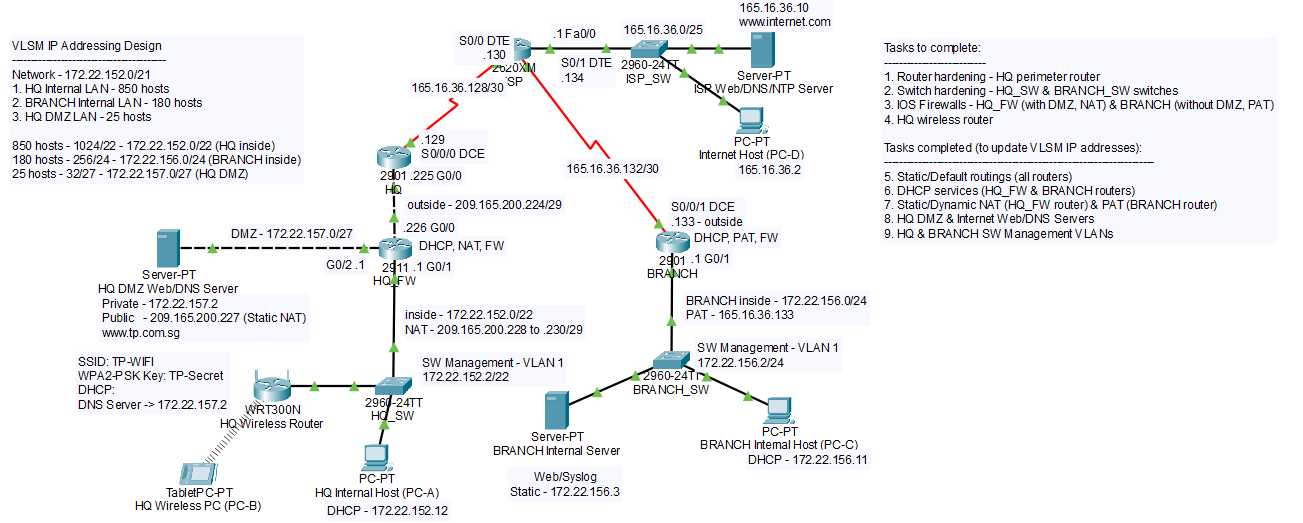
- Cisco Packet Tracer was used again in NWS assignment to simulate a network topology of a company with 1 branch and 1 HQ.
- In Network Security module, we learnt how to configure Zone-based Policy Firewall (ZPF), Access List Control (ACL), Network Address Translation (NAT), Network Time Protocol (NTP) and System Logging Protocol (Syslog).
- The Variable Length Subnet Mask (VLSM) IP addressing scheme was used to assign IP addresses to each network devices.
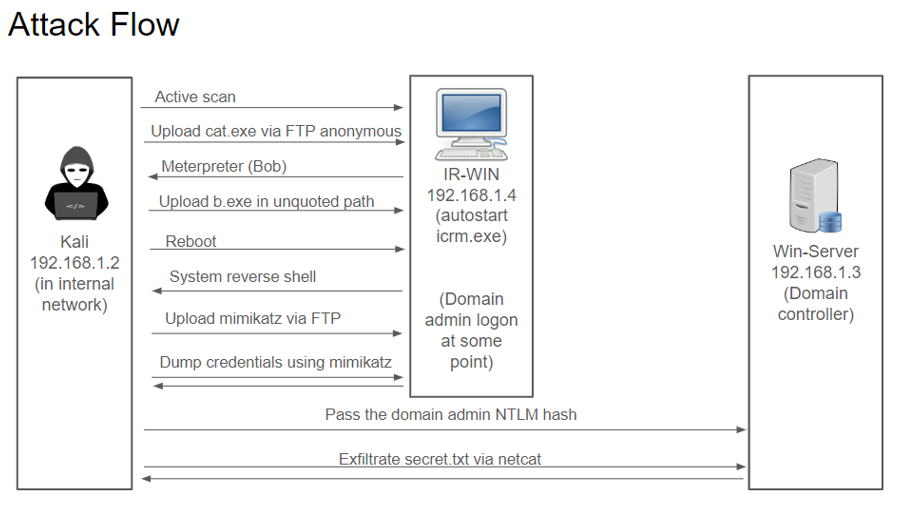
- Incident Response and Management module exposed me to WireShark (a network traffic packet analyzer), Splunk (a platform for for monitoring and analyzing machine data), Snort rules for defining malicious network activities and raising alerts.
- In the group project, we referenced to the MITRE Attack Navigator to demonstrate attacks progressing from Reconnaisance, Execution, Privilege Escalation, Lateral Movement to Exfiltration in an Active Directory environment.
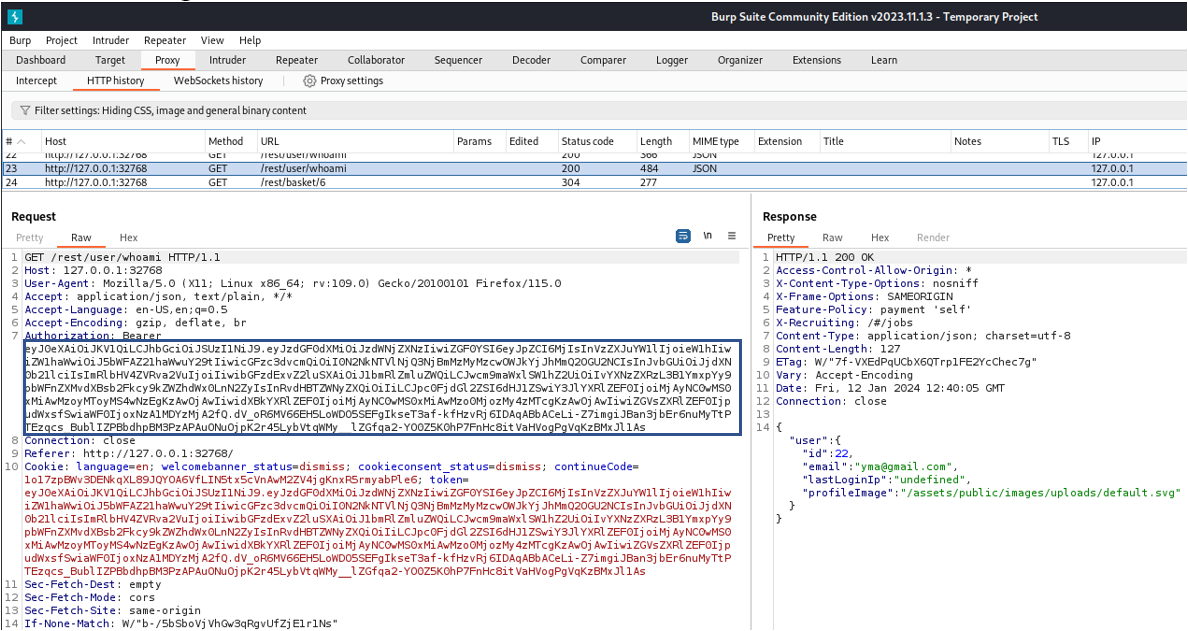
- The Burp Suite Community Edition is an application security testing software that sets up a proxy to analyze requests and responses between the browser and the target application.
- The Secure Web Application module taught us how to conduct different types of testing such as unit testing, integration testing, performance testing, and penetration testing on a website using tools such as SonarLint in Eclipse, Apache JMeter, Google Lighthouse in Chrome, and Burp Suite.
- Referencing to the OWASP Top 10 in 2017 and 2021, the project tasks were to find vulnerabilities and exploit them in OWASP Juice Shop website hosted on a docker.
- AppSheet is a no-code development platform for creating application from data sources like Google Drive, Spreadsheet and other database platforms.
- Apps Script is a scripting platform for light-weight application development in the Google Workspace platform.
- In Guided Learning project, I created some automation scripts that involves creating and copying folders in Google Drive, copying data in Sheets, generating pie charts and adding numbers into Google Contact from a sheet.
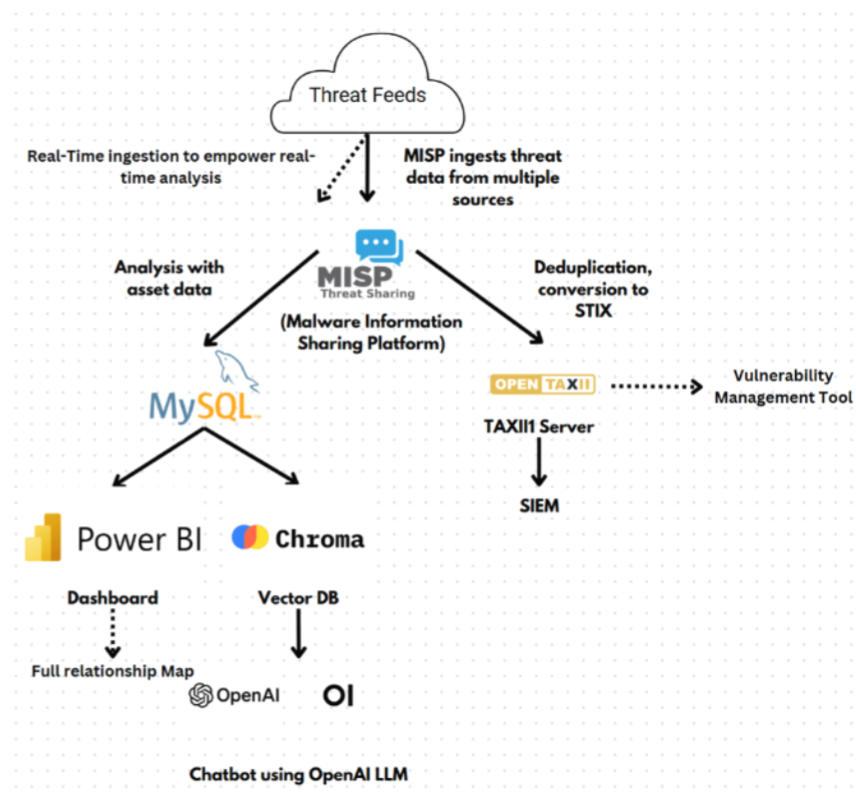
- A Threat Intelligence Platform (TIP) is a cybersecurity tool that collects, analyzes, and provides actionable insights about potential cyberattacks.
- MISP is an open source software solution for collecting, storing, distributing and sharing cyber security indicators and threats about cyber security incidents analysis and malware analysis.
- Trusted Automated Exchange of Intelligence Information (TAXII) is an application protocol for exchanging CTI over HTTPS.
- Leveraged MISP and TAXII to ingest and store threat intelligence. Analyzed threat data to identify relevant information for the organization. Utilized Power BI to visualize key threat insights. Integrated OpenAI with ChromaDB and Open WebUI to enable advanced threat query and response capabilities.
- This major project was selected to present in the TP Infotech day 2025. Please see a demo video at https://youtu.be/dpt_X26fsjQ.
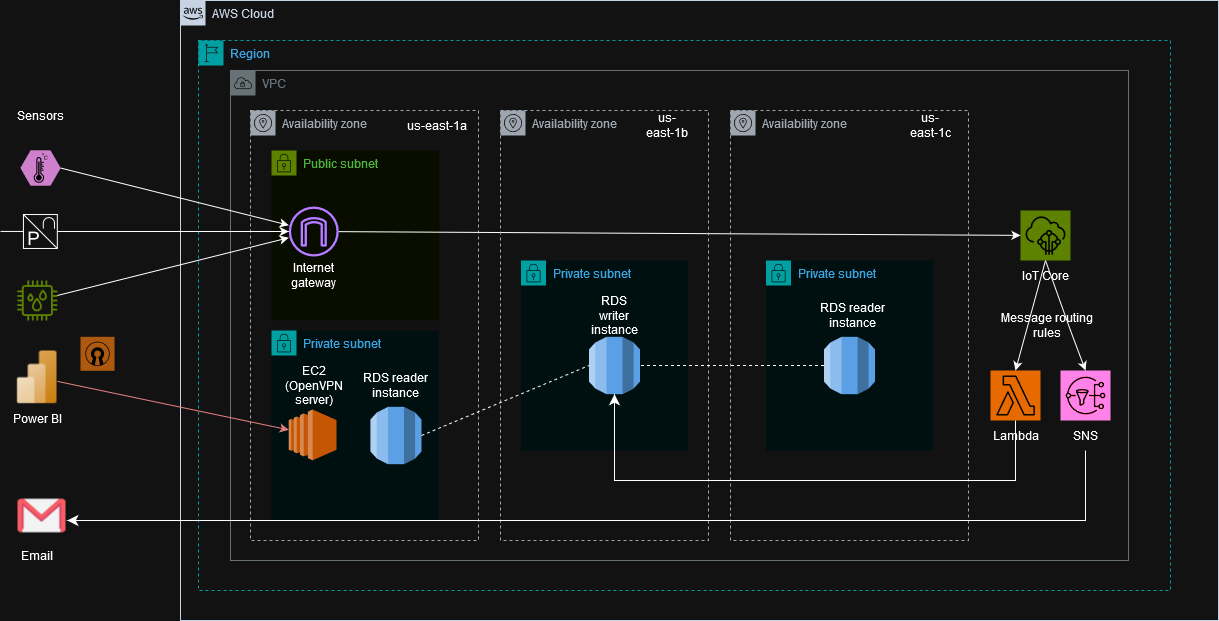
- AWS is the cloud platform offered by Amazon.com Inc which provides services such as compute, storage, networking, analytics and security.
- The project involves sensor simulation scripts, MQTT (Message Queuing Telemetry Transport) which is a lightweight, publish-subscribe messaging protocol that enables communication between devices, AWS services, and Power BI.
- This project architecture ensures security and high availability since there are multiple availability zones, multiple RDS instances (writer, reader) and RDS is placed in private subnet for isolation.

- UiPath is a robotic process automation (RPA) software that can do browser automation, app automation, screen scraping, data entry, and website testing.
- I got familiar with UiPath in my internship by creating multiple RPA processes for privileged account onboarding/offboarding, checking reputation of IP addresses and vulnerability remediation scans.